
protocol theory - Where is Ping's "round-trip time" stored in the IP header? - Network Engineering Stack Exchange
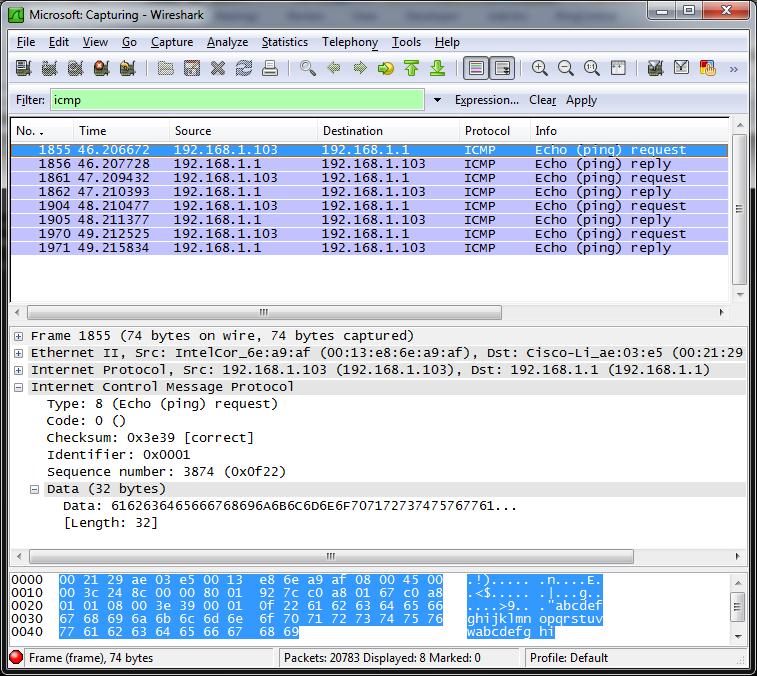
The Anatomy of a Packet Path (ICMP) from Source to Destination | The Anatomy of a Packet Path (ICMP) from Source to Destination | Pearson IT Certification
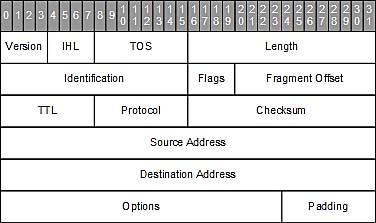
The Anatomy of a Packet Path (ICMP) from Source to Destination | The Anatomy of a Packet Path (ICMP) from Source to Destination | Pearson IT Certification
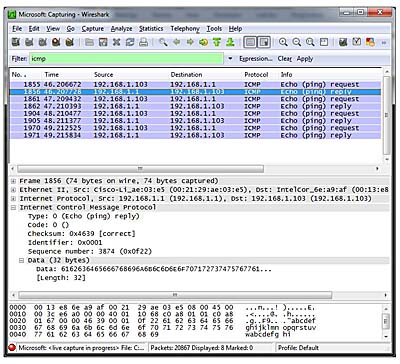
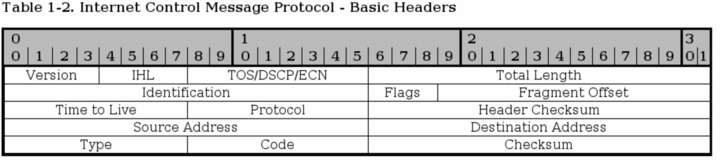

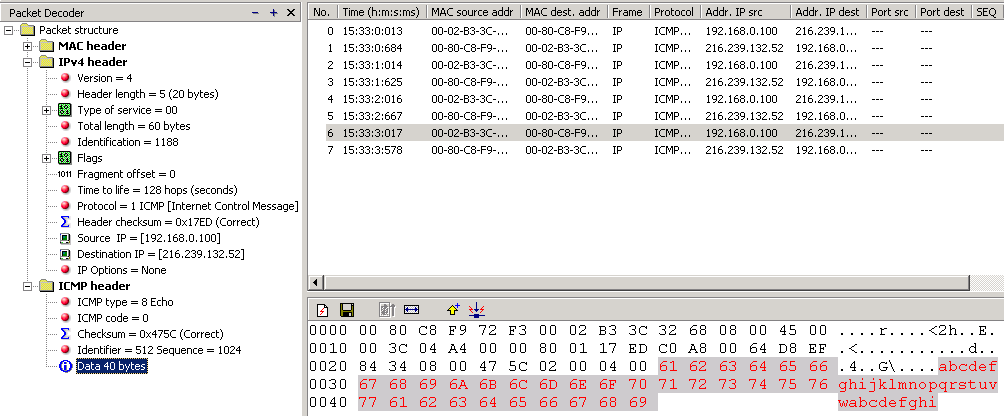
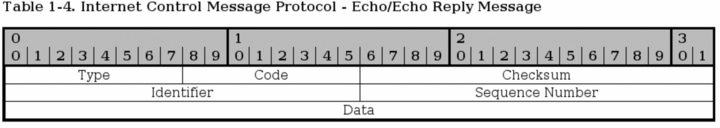


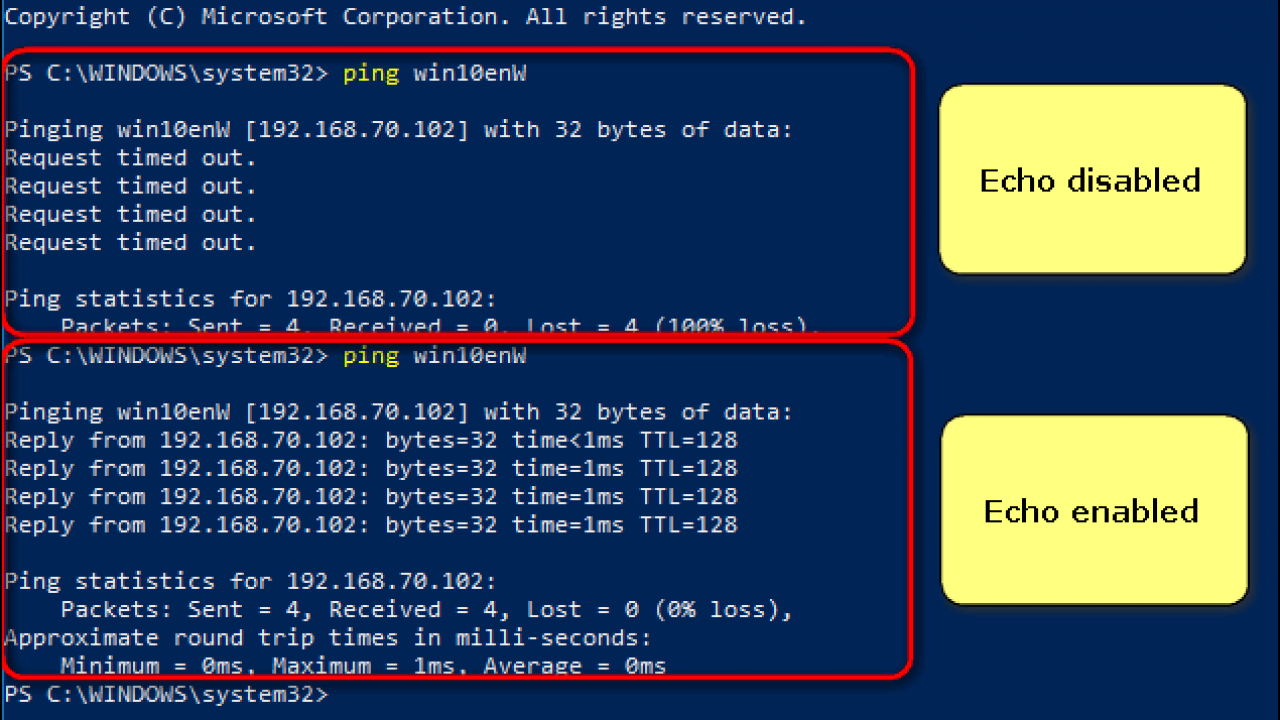
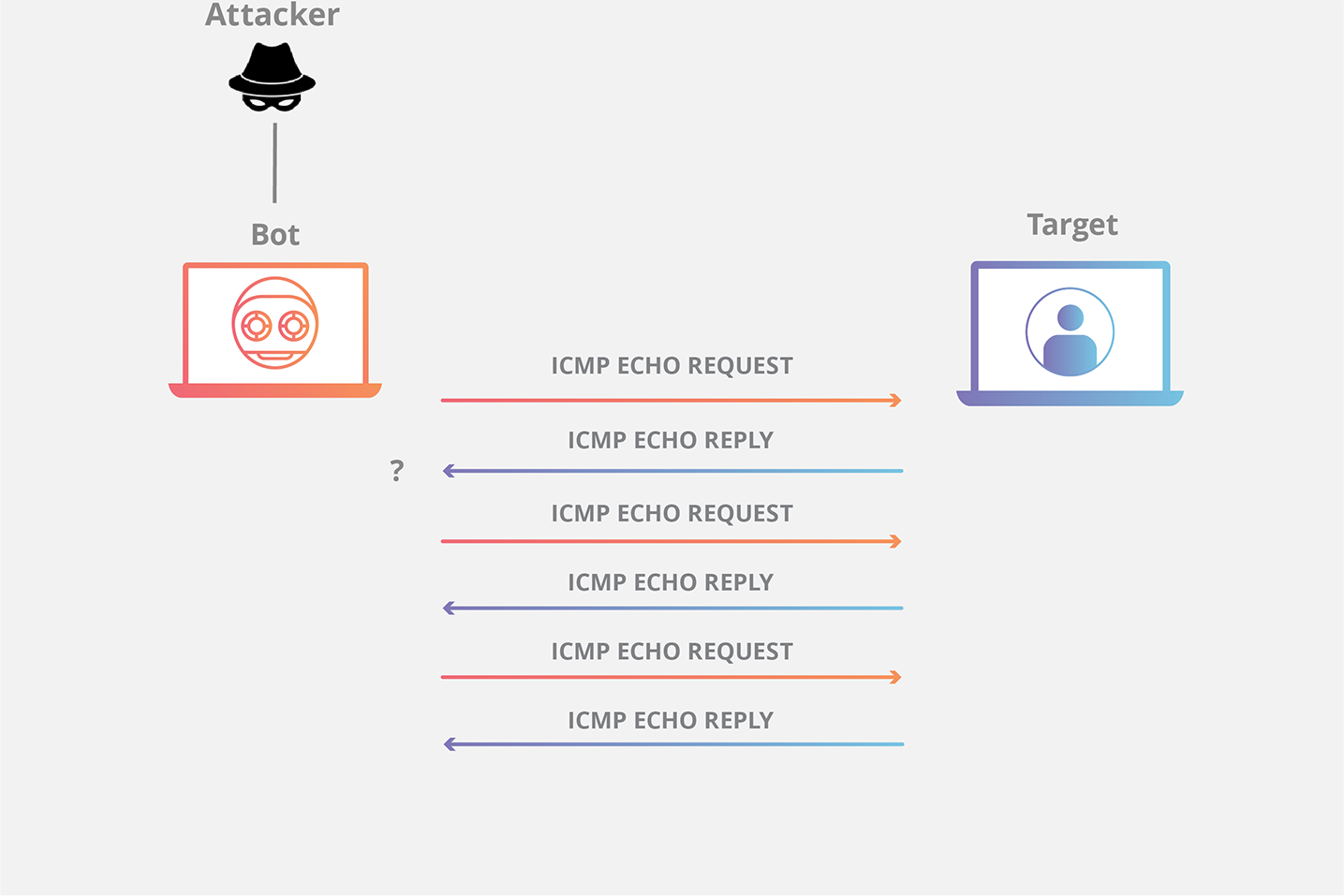
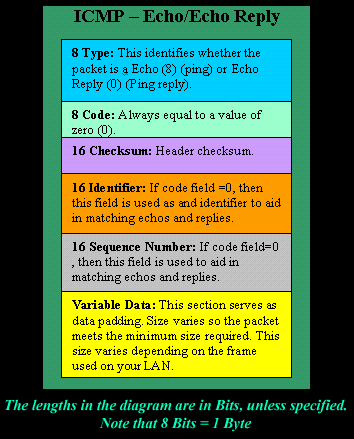
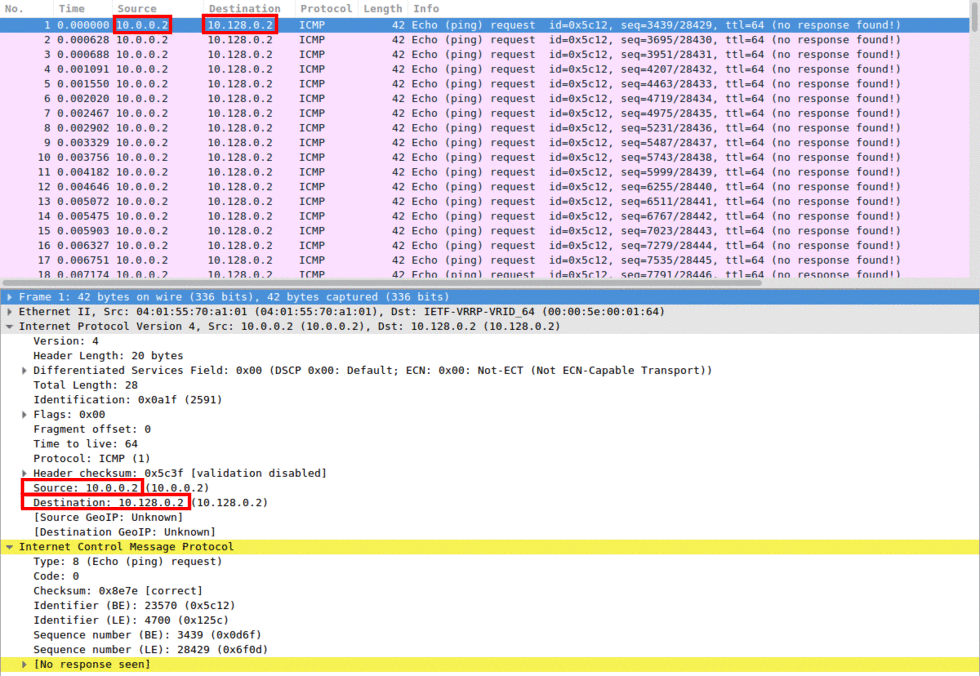

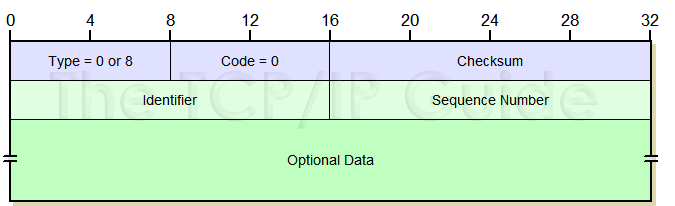

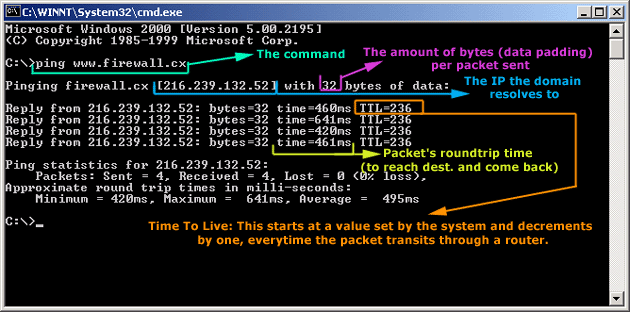

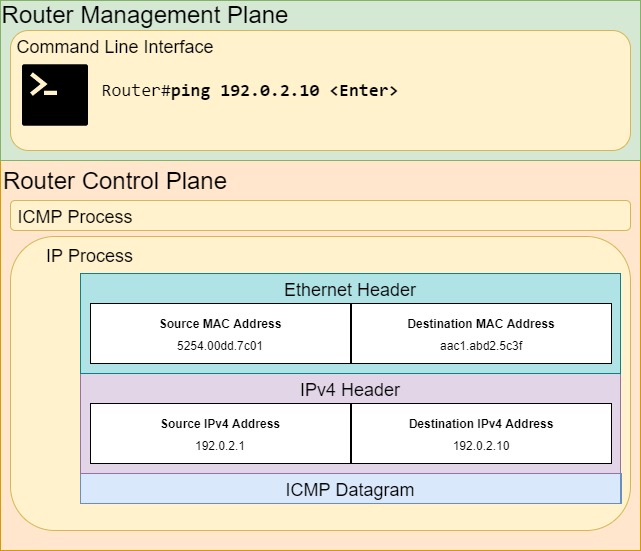
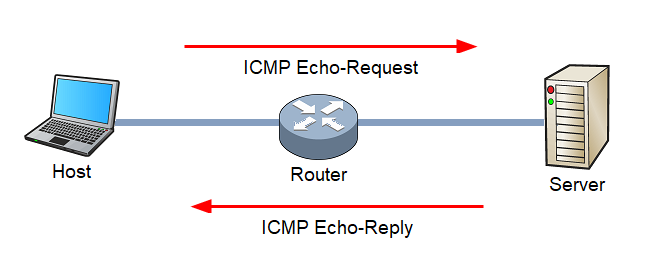

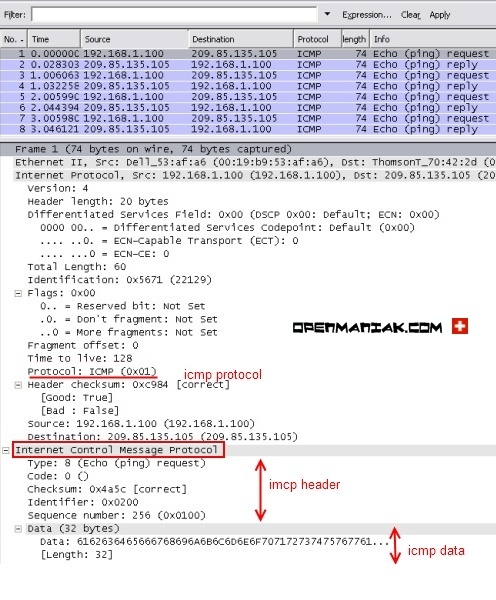
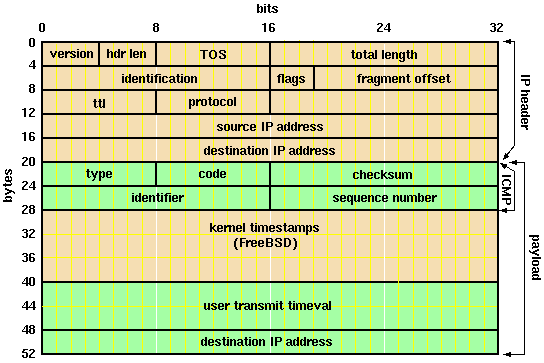
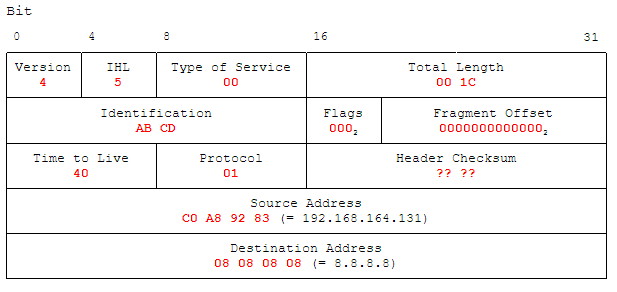

![ICMP echo request - Industrial Cybersecurity [Book] ICMP echo request - Industrial Cybersecurity [Book]](https://www.oreilly.com/api/v2/epubs/9781788395151/files/assets/a9059c5d-2c94-4d48-80d5-b42450fff6ab.jpg)
