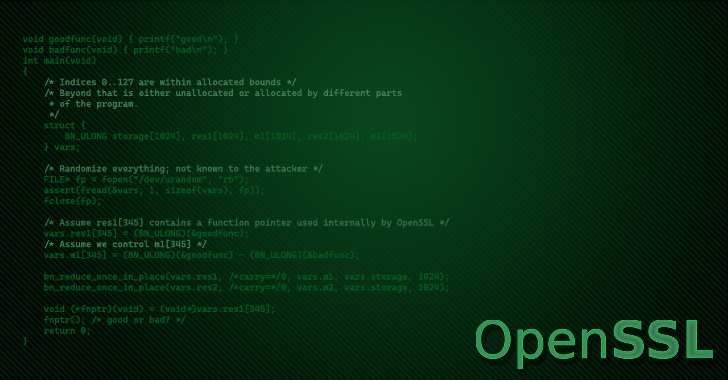
Memory Leak Tutorial | What is Memory Leak | Memory Leaks and Memory Leakage explained with Example - YouTube
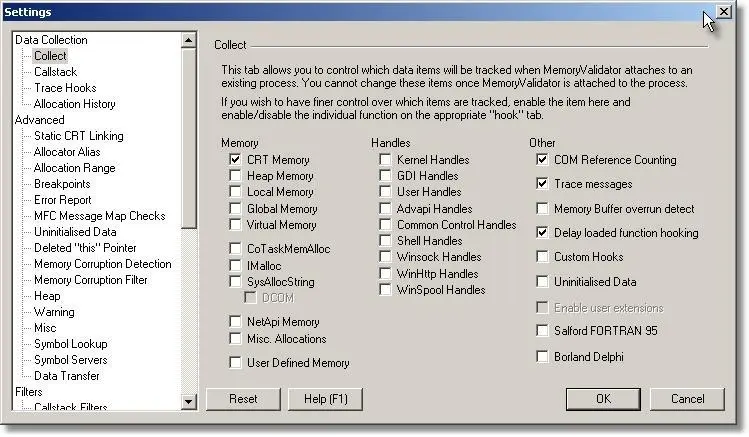
Memory Validator Tutorial - How to detect memory corruption (tools) using Memory Validator. | Software Verify

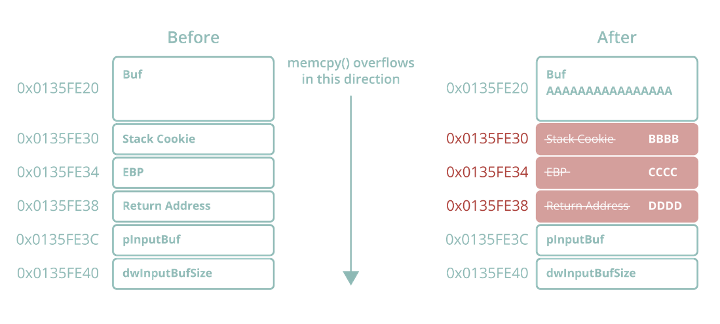
State transition of a randomized program under a memory corruption attack | Download Scientific Diagram
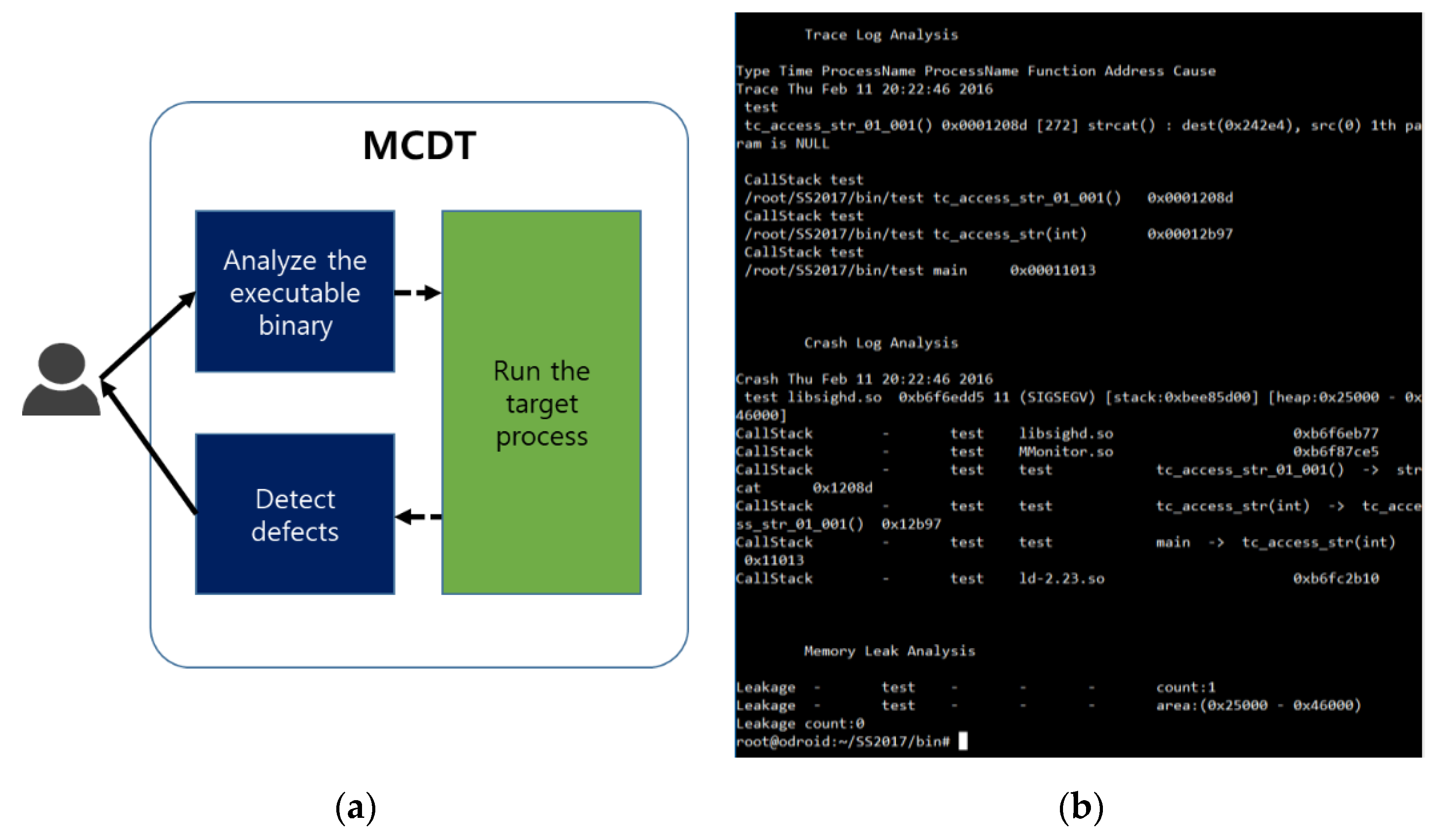






![PDF] Automatic diagnosis and response to memory corruption vulnerabilities | Semantic Scholar PDF] Automatic diagnosis and response to memory corruption vulnerabilities | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/652be28ce9fb95e48c5233327dda0850c00ac90e/2-Figure1-1.png)