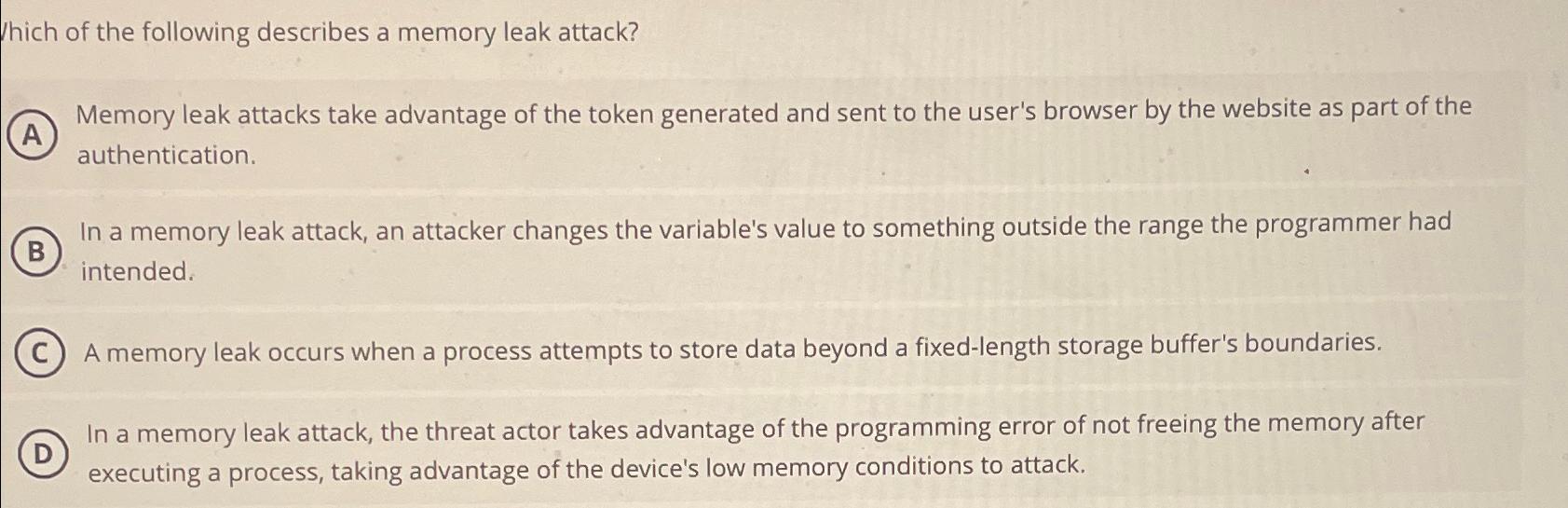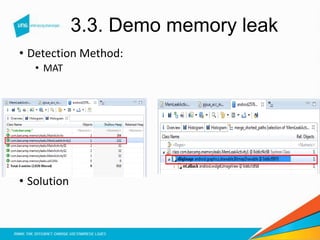
VIDEO solution: Wich of the following describes a memory leak attack? Memory leak attacks take advantage of the token generated and sent to the user's browser by the website as part of

Applied Sciences | Free Full-Text | SGXDump: A Repeatable Code-Reuse Attack for Extracting SGX Enclave Memory
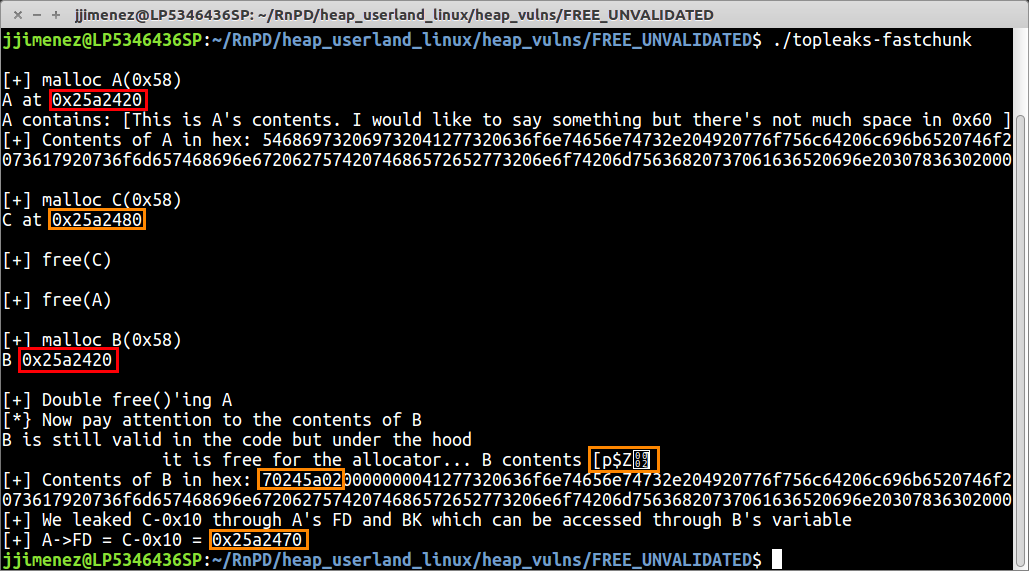
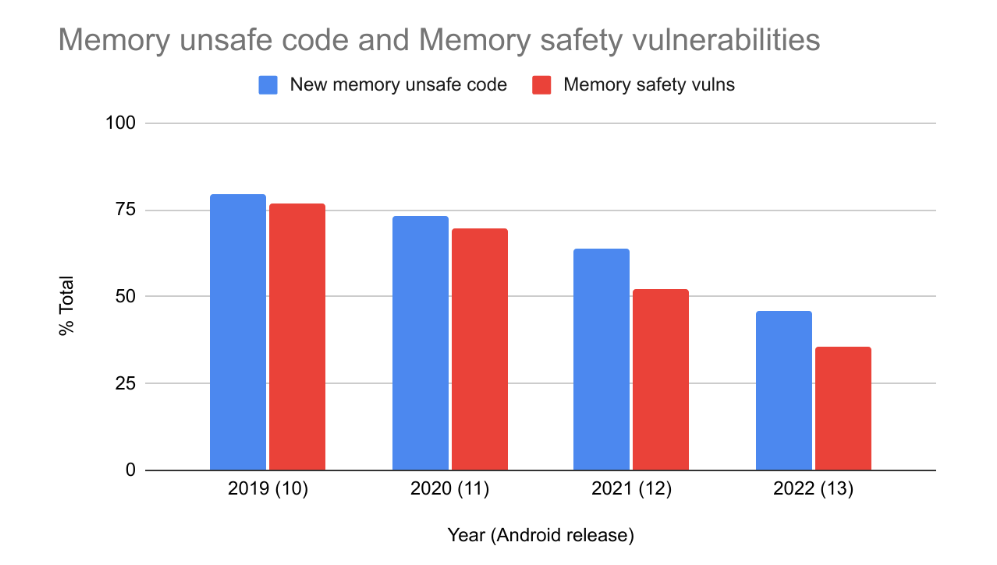
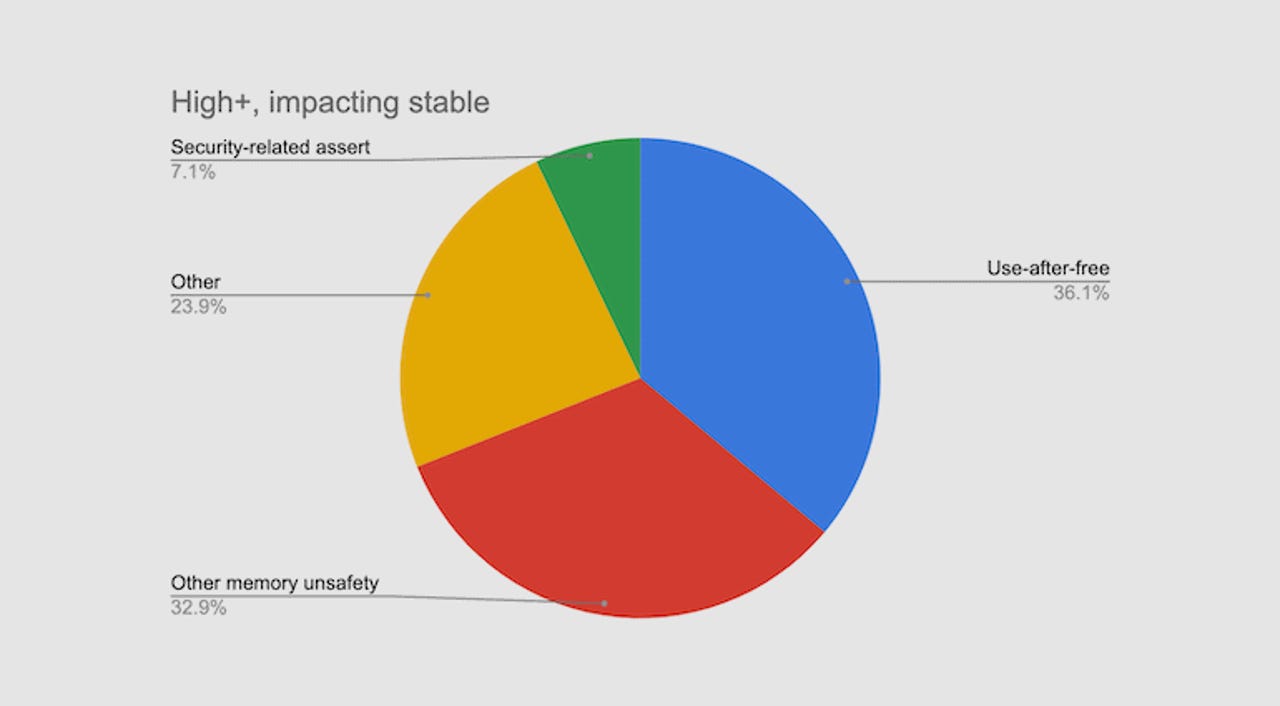
Part 6 — My Talk “The Evolution Of Exploiting Memory Vulnerabilities In Linux” | by Ofri Ouzan | Medium

How memory leaks leave the door open for hackers and how Functional Programming can remedy that - Ada Beat